Cybercriminals and Russian state-backed hacking groups will almost certainly try to disrupt energy infrastructure, including renewables, in the coming year
This assessment was issued to clients of Dragonfly’s Security Intelligence & Analysis Service (SIAS) on 18 October 2024.
- Since 2022, most cyberattacks on Europe’s energy infrastructure have affected IT systems rather than operational technology (OT), which controls physical processes
- Financially motivated ransomware groups are likely to remain the main perpetrators of hostile cyber operations against energy companies
Russia will probably remain the main state actor conducting and sponsoring hostile cyber operations against Europe’s energy sector into 2025. State-backed hackers have breached multiple energy firms since the start of the Ukraine war, but these mainly affected IT systems instead of physical infrastructure. While such attempts have tended to garner media attention, most cyber intrusions into Europe’s energy sector are unlikely to disrupt power generation. Ransomware groups will probably continue to pose the greatest threat to energy firms in the coming years.
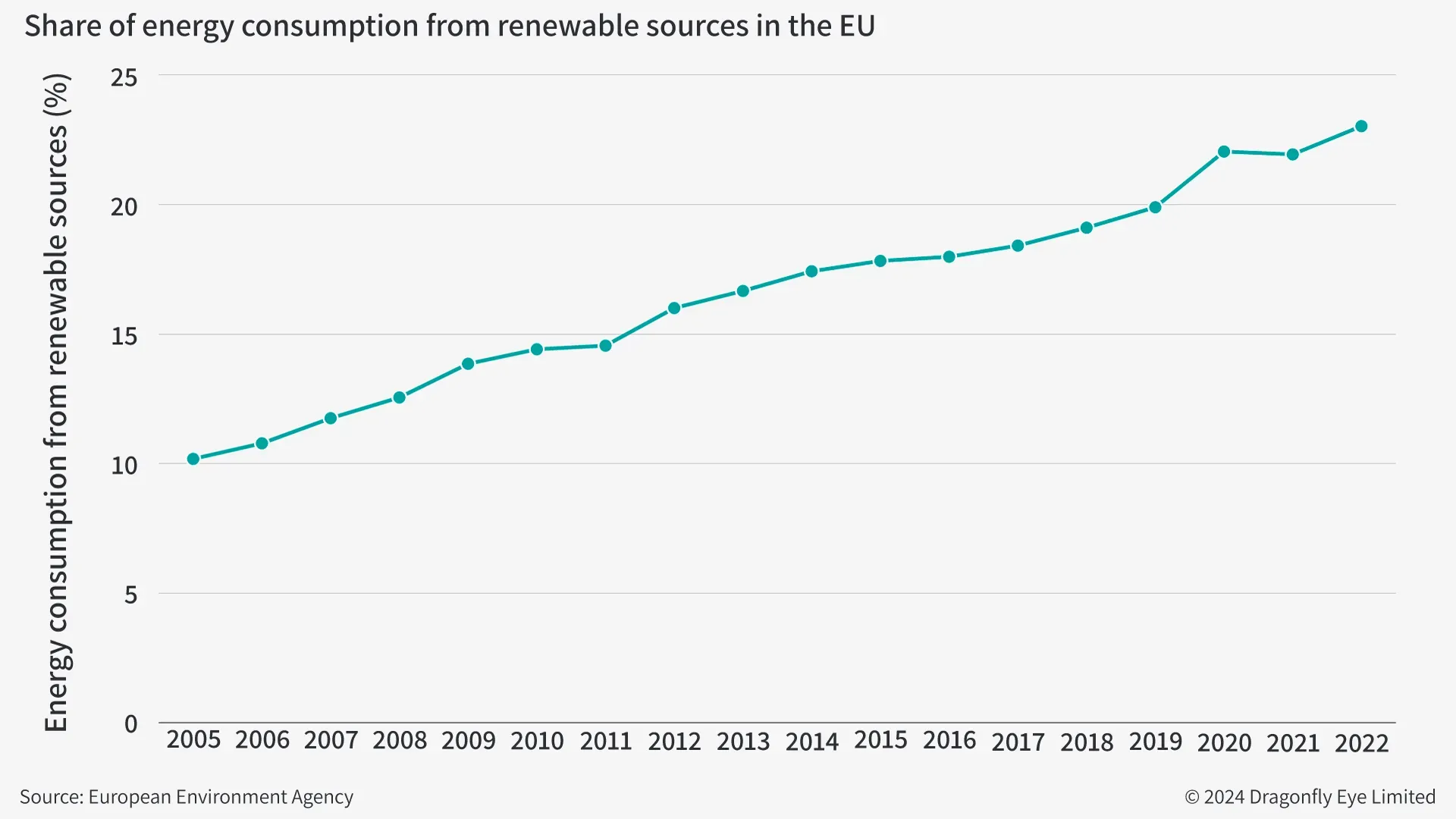
Renewables firms are also highly likely to come under threat from both state hacking groups and cybercriminals. The growing importance of this sector in meeting Europe’s energy needs (see above graphic) will probably make it a more appealing target for both Russian state-backed groups and financially motivated cybercriminals.
Russian threat to Europe’s energy sector
Russia’s broader aims in Europe are to sow discord, diminish public trust in European governments and undermine public support for Europe’s backing of Ukraine. Cyberattacks (as well as physical sabotage) against the energy sector have been among the ways it has pursued this. Since the start of the war in 2022, there have been at least ten publicly reported breaches by Russian state-backed hacking groups, according to our monitoring. The largest among these was a cyber operation against 22 energy firms in Denmark in April.
That said, we doubt that Russian cyberattacks against Europe’s energy infrastructure this winter would cause substantial physical damage or loss of life. Past cases have shown this is possible – in 2014, unidentified hackers caused ‘massive damage’ to a furnace at a German steel mill. And Russia in 2022 remotely tripped circuit breakers at a substation in Ukraine, causing a power outage. But Ukraine will probably be the focus of Russia’s cyber operations this winter. Confirmed cases of Russian hackers gaining control of operational technology (OT) in other countries have been rare.
Cyberattacks causing physical damage to remain very rare
The most probable effects of Russian state-backed cyberattacks would be disruption to IT systems such as smart grids. The vast majority of cyberattacks on Europe’s energy infrastructure in the past two years have only affected IT systems. While this could hinder some operational processes, they are unlikely to severely disrupt the power supply to homes or businesses. Cybercriminals and other non-state hackers usually do not have the motivation or capability to breach OT in energy infrastructure.
Russian state-backed cyber operations that disrupt physical processes in Europe’s energy sector will probably remain very uncommon into 2025. Many OT systems are ‘airgapped’, meaning they are not connected to the internet and so harder for attackers to access remotely. And industrial facilities tend to have multiple physical safeguards.
There is evidence of resilience. A Russian state-backed group claimed in March to have sabotaged a hydroelectric power plant in France. But it only succeeded in causing a minor drop in water levels upstream of a small mill. The operator of the plant said after the event that physical safeguards like a spillway would have prevented overflow.
Hackers use simple tactics to access critical systems
Most successful attempts to infiltrate critical systems in the energy sector will probably use simple methods. This includes password guessing or entering default credentials that have not been changed from factory settings. The US Cybersecurity and Infrastructure Security Agency (CISA) on 25 September issued a warning to this effect, saying that hostile cyber actors globally were actively exploiting OT that is connected to the internet with these tactics. On this basis, hackers targeting European energy infrastructure are likely to do the same.
Renewables sector vulnerable to cyberattacks
Russian state-backed groups and financially motivated cybercriminals globally will almost certainly try to breach renewable energy firms in the coming year. The portion of EU energy consumption from renewables has risen by around 1% each year since 2005 and was at 23% as of 2022, the latest year for which this data is available. Growing reliance on solar and wind power means state-backed cyberattacks would be more disruptive to energy supply. And industry growth makes these firms a potentially lucrative target for cybercriminals. Recent cases include:
- Russian state-backed hackers claimed a cyberattack on a Lithuanian renewable energy firm in September
- Russian state-backed hackers breached a small hydroelectric power plant in France in March
- Multiple ransomware groups breached green energy firms in Germany and Denmark throughout 2023
- A UK-based cybersecurity firm found in a report this year that renewables firms in the UK face up to 1,000 attempted cyberattacks each day. It did not specify who was behind these, but most probably originated from cybercriminals as state-backed cyber operations are comparatively rarer
Many parts of renewable energy infrastructure also appear to be highly vulnerable to cyberattacks. This is because much of it is consumer-facing and requires remote monitoring, such as solar panels installed on houses. As such, it incorporates a lot of WiFi-enabled Internet of Things (IoT) devices. These tend to have weak cyber defences that make them prone to being exploited by hackers. Deloitte estimates that around 70% of IoT devices come with very simple default passwords, and the majority of users never change them.
Ransomware remains biggest threat to energy firms
Financially-motivated ransomware groups are likely to remain the main perpetrators of hostile cyber operations against the energy sector in the coming years. Our monitoring of publicly reported cases suggests there is not usually a substantial spike in ransomware attacks during winter months, despite there being more public pressure for energy firms to provide uninterrupted service in winter.
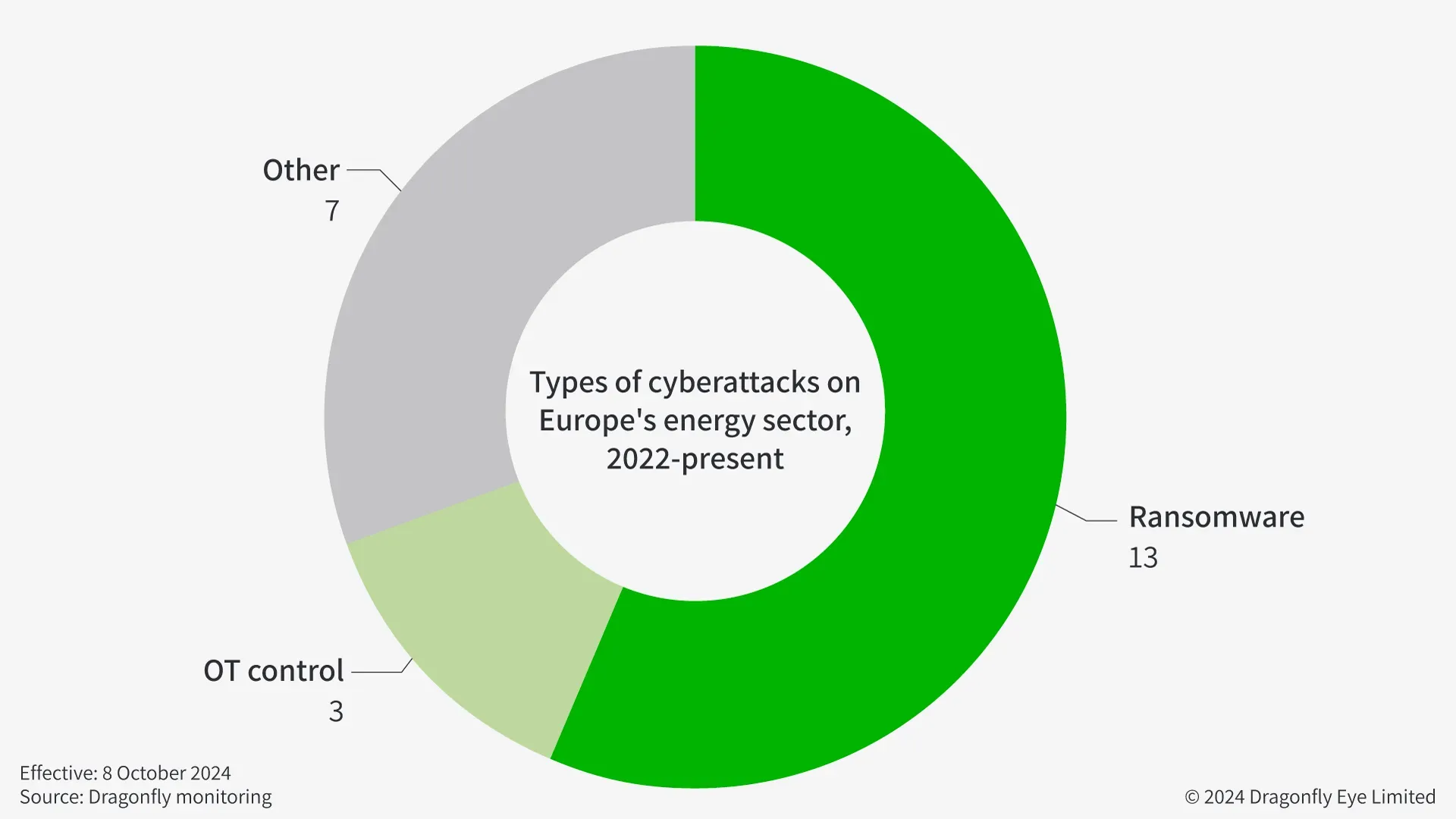
Cybercriminals are largely opportunistic and financially motivated. The energy sector will remain a highly attractive target as it often operates using legacy systems that are no longer receiving regular updates and cybercriminals perceive these firms to be wealthy. Ransomware would affect IT systems and are unlikely to disrupt OT, in our view. But such incidents could still temporarily suspend or slow down some business operations such as payment processing if attackers encrypt files or delete data.
Image: Illustration picture shows a visit to the center for cyber security in Belgium (CCB) in Brussels, Wednesday 30 November 2022. Photo by Hatim Kaghat/Belga Mag/AFP via Getty Images.




