China seems to be making very long term (beyond five years) cyber preparations to disrupt critical infrastructure in the US in the event of a conflict
This assessment was issued to clients of Dragonfly’s Security Intelligence & Analysis Service (SIAS) on 29 April 2024.
- US federal agencies have expressed alarm at China-sponsored groups attempting to access the IT systems of US pipelines and telecommunications firms among others
- The US authorities are likely to struggle to deter offensive Chinese cyber operations
Chinese state-sponsored cyber actors are likely to mount near-daily attempts to infiltrate US telecommunications, energy, and water utilities sectors. That is along with other critical infrastructure and associated industries. US officials have recently said that China is developing the ‘ability to physically wreak havoc’ on critical infrastructure. But China would probably only use it to cause severe disruption in the case of a major conflict with the United States. In our analysis – and based on its focus on infiltration rather than destruction so far – China is seeking leverage to deter the US in the future rather than escalate now.
China highly intent to target critical sectors
The Chinese state seems to be behind a major ongoing hacking campaign. The US government has dubbed this Volt Typhoon. While it may be orchestrated by a single hacking group, it is more plausible that multiple groups are ultimately involved, because of the many IP addresses associated with these operations. Based on recently reported cases, the hacking campaign appears to be targeting a wide range of industries, including:
- Telecommunications firms
- Pipeline operators
- Electrical grid operators
- Ports
- Water utilities
Several of these industries often rely on IT systems that are multiple decades old. This leaves them vulnerable to cyberattacks as they are no longer being updated. The campaign appears to be on a fairly large scale too. For example the FBI disclosed on 18 April that Volt Typhoon had successfully gained access to 23 US pipeline operators. Although that is only a small portion of the approximately 3,000 such firms in the US, the number of undiscovered intrusions is likely to be several times greater in our view.
Volt Typhoon campaign unlikely to lead to day-to-day disruption
China is unlikely to cause severe physical disruption to US critical infrastructure any time soon. Despite their presence in these networks, there are no public reports of Volt Typhoon trying to extort victims or disrupting physical operations in the US. And in 2023, Volt Typhoon intrusions were discovered in a wide range of firms including an unnamed major West Coast port and a water utility firm in Hawaii. But none of these intrusions affected the industrial control systems (ICS) that operate critical functions or caused a disruption.
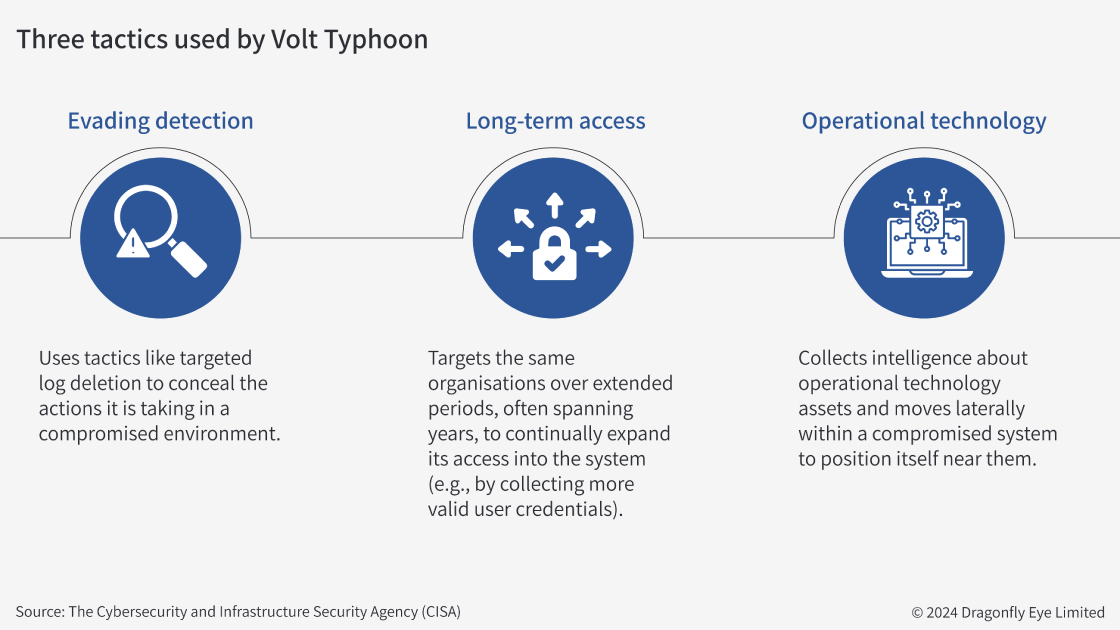
These intrusions are, in our analysis, part of a longer-term cyber strategy rather than an attempt to cause current damage. This is apparent in two of Volt Typhoon’s tactics: evading detection and establishing long-term access to a target (see graphic above). US government reports from this year suggest it attempts to maintain and expand access to systems over months or years. The hackers do this by primarily exploiting vulnerabilities in public-facing applications like email servers to gain initial access to a victim’s IT system.
Volt Typhoon could cause severe disruption in the US. This would potentially include severing communications and polluting water systems. Volt Typhoon’s tactic of positioning itself near operational technology assets in a compromised network makes this possible. However, in our assessment, China is seeking these capabilities as part of very long-term preparations (beyond five years), rather than because it has specific plans to use them. They would probably be used to disrupt critical infrastructure during a major US-China confrontation or to constrain the US’ ability to take punitive action against China.
State scrutiny of critical industry cybersecurity
The US is likely to step up its response. Since January, US federal agencies have made multiple statements expressing alarm at the scale and persistence of Volt Typhoon intrusions. US government agencies are working with industry to track and respond to individual threats. In recent years the US authorities have responded with congressional hearings, botnet takedowns, and sanctions against suspected Chinese state-sponsored hackers. But according to the Cybersecurity and Infrastructure Security Agency (CISA), those have had no effect on Volt Typhoon’s behaviour.
The US will probably introduce more stringent regulations or legislation to boost cyber resilience. That would be along the lines of the Health Care Cybersecurity Improvement Act of 2024. New legislation would be likely to apply to affected sectors (telecommunications, pipelines, electrical grids, ports and water utilities) and companies that provide services to them, as some Volt Typhoon intrusions originated in third-party suppliers. For example, the Coast Guard has already proposed measures to strengthen the cyber resilience of the maritime sector’s supply chain.
Image: A mobile phone displaying the logos for Chinese apps WeChat and TikTok in front of a monitor showing the flags of the United States and China in Beijing, China, on September 22, 2020; Photo by Kevin Frayer/Getty Images.




