- The cyber threat to US organisations from Iran’s state-linked groups is likely to remain high over the coming year
- On 30 June, the US federal agency responsible for cyber security stated that Iran-aligned hacking groups ‘may still conduct malicious cyber activity’ against the US, despite the ceasefire between Iran and Israel
- Iran-linked cyber actors are likely to continue using Telegram to spread exaggerated or false claims of cyberattacks this year on US utilities, consistent with past information operations
Pro-Iran cyber groups are highly likely to remain a persistent threat to critical infrastructure and defence firms in the US over the next year. These groups intensified their operations in June, during the 12-day war between Iran and Israel, based on activity we have observed on Telegram. On 30 June, the US Cybersecurity and Infrastructure Security Agency (CISA) warned that cyber activity by Iran-aligned actors is ‘expected to escalate’, advising US organisations to ‘remain vigilant’.
Iran’s direct cyber response to the US military strikes on Iranian nuclear sites on 22 June seems to have been limited. This is despite widespread media speculation about potential Iranian state-backed retaliation. Yet a joint advisory issued by US intelligence sharing centres on 13 June has urged firms to prepare for ‘the likelihood of increased cyber attacks from Iran’. The US-brokered ceasefire between Iran and Israel agreed on 23 June appears to be holding. However, the recent conflict and direct US involvement will probably motivate Iran’s state-linked cyber groups to prioritise gaining access to US critical infrastructure in the coming months.
Lack of disruptive response from Iran
There is no clear evidence of a surge in Iranian state-sponsored cyberattacks on the US during the Iran-Israel conflict or following the 23 June ceasefire. For instance, American cyber intelligence sharing centres said on 23 June that they had not seen any confirmed operations from Iran targeting US companies. Several cybersecurity firms and specialist news outlets have corroborated this.
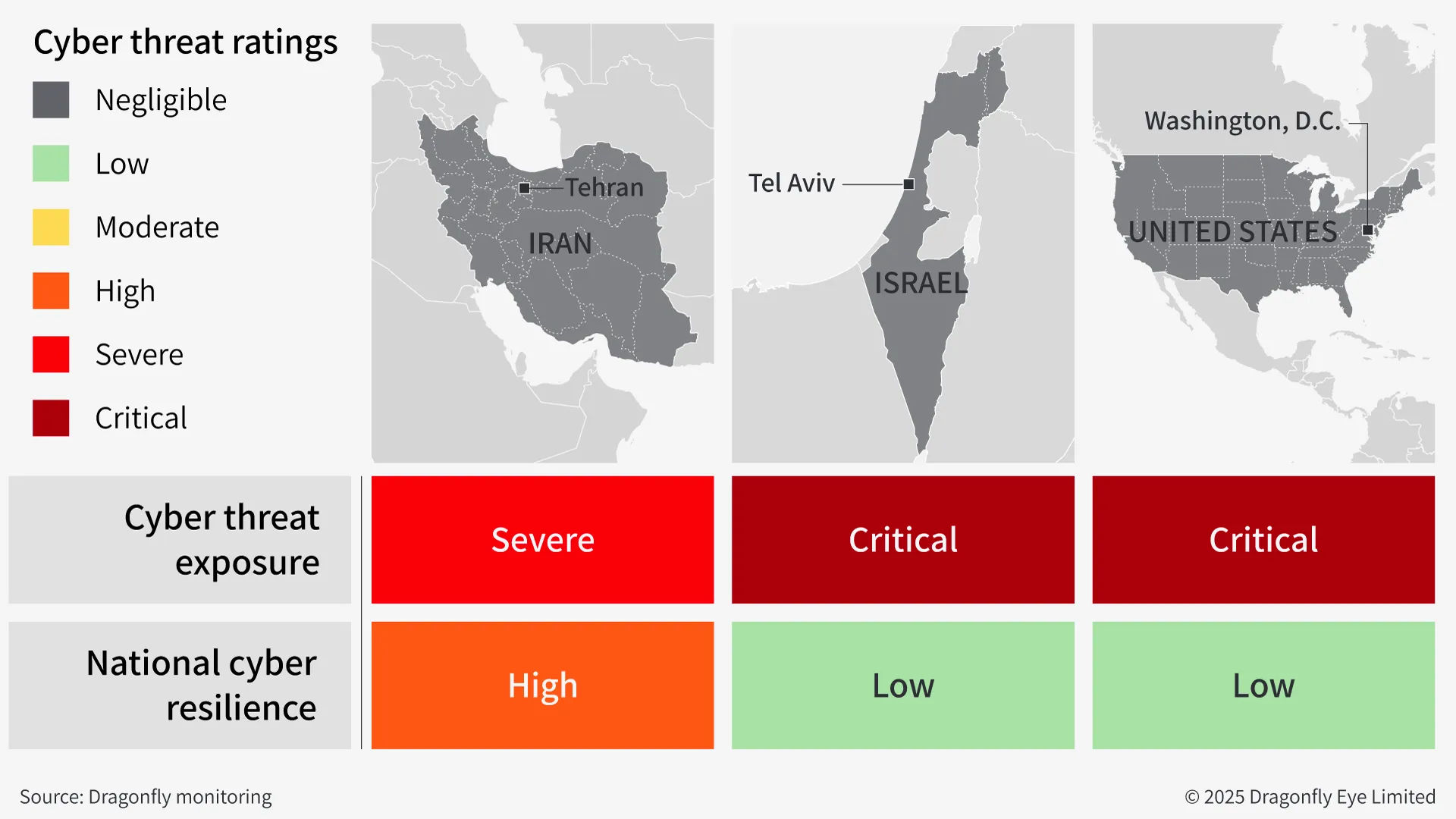
Tehran’s lack of a direct response contrasts with the high volume of Iran-linked cyber operations targeting Israel during the June conflict. In recent weeks, pro-Iran groups, including some linked to the state, claimed DDoS attacks, data leaks, and to have disrupted operational technology such as water treatment systems in Israel, many of which are unverified. While some hacktivists in support of Iran claimed DDoS attacks against US organisations on Telegram, there have been few claims from state-linked channels.
Instead, Iran seems to be leveraging information obtained in past cyber operations. Reuters reported on 30 June that IRGC-linked hackers told journalists they planned to sell emails stolen from people linked to President Trump, including one of his lawyers and chief of staff. The same group is very likely responsible for having distributed similar emails before the US presidential election in 2024. And this tactic is probably a way for Iran to inflict costs on the US for its military actions by releasing data it has already acquired.
Iran still a disruptive threat
Still, Iran will probably try to target US government networks or critical infrastructure operators in the coming months. With a probable resumption of talks between the US and Iran over the latter’s nuclear programme, this would be a way for Iran to pressure the US without prompting a military escalation. The intensity of Iranian offensive operations against the US in recent years has appeared to be correlated to the status of US-Iran relations. And Iran has previously used cyber operations as a key tool to respond to real or perceived aggressions.
Any Iranian operations would probably include attempts to disrupt utilities or deploy data-wiping malware against organisations. Recent US CISA guidance highlighted the potential threat to US defence industrial companies, especially those with links to Israel. And in 2023, the IRGC-linked group CyberAv3ngers conducted a campaign targeting operational technology systems in the US, including Israeli-made Unitronics programmable logic controllers (PLCs) at water facilities.
Iran’s cyber operations targeting critical infrastructure in the US in recent years have appeared to focus on exploiting vulnerable internet-connected devices. CISA said in its 30 June guidance that such groups ‘routinely target poorly secured US networks and internet-connected devices.’ And when CyberAv3ngers accessed Unitronics PLCs, they compromised devices with a default or no password – a relatively simple way to gain access. Disruption was generally mitigated by the facilities. Any further operations against US critical infrastructure would probably follow a similar pattern.
Such groups are also highly likely to exaggerate the impact of their claims. CyberAv3ngers has a track record of doing so, including a seemingly fabricated claim that it breached a power plant in Israel in 2023. This seems to be part of a trend of combining limited cyber capabilities and influence tactics to maximise public and media attention.
Iran likely to double-down on espionage
Cyberespionage and gaining initial access to critical US networks is likely to be a top priority for Iran in the coming months. The recent conflict has probably increased Tehran’s motivation to try to position itself in Western critical infrastructure networks for future operations. This would especially be for campaigns that would provide it with an advantage during any future military conflict. In CISA’s recent advisory, it highlighted the defence industry, especially those with links to Israel, as likely priority targets for Iran or Iran-linked cyber operatives in general.
 We have seen no recent evidence that Iranian cyber groups are currently engaging in campaigns to acquire and maintain long-term access to US networks. Multiple reports by US officials in recent years have warned that Chinese state cyber groups are pre-positioning themselves in these. Iran’s offensive cyber capabilities are very probably less advanced than China’s. However, the US intelligence community has previously warned that Tehran is continuing to develop its capabilities. In its annual threat assessment, issued in March, the US assessed that Iran’s growing expertise and willingness to conduct ‘aggressive cyber operations’ make it a major threat to the security of US networks and data.
We have seen no recent evidence that Iranian cyber groups are currently engaging in campaigns to acquire and maintain long-term access to US networks. Multiple reports by US officials in recent years have warned that Chinese state cyber groups are pre-positioning themselves in these. Iran’s offensive cyber capabilities are very probably less advanced than China’s. However, the US intelligence community has previously warned that Tehran is continuing to develop its capabilities. In its annual threat assessment, issued in March, the US assessed that Iran’s growing expertise and willingness to conduct ‘aggressive cyber operations’ make it a major threat to the security of US networks and data.
Image: People show the Iranian messaging app (Bale) on their mobile telephones in Tehran, on 19 April 2023. Photo by Atta Kenare/AFP via Getty Images.




